Secure encryption is the key to trust and data protection in e-commerce. Here are the key insights:
- TLS/SSL protects data during transmission, visible through “https://” and the lock symbol. Current standard: TLS 1.3.
- AES-256 efficiently secures stored data and is recommended for credit card data.
- RSA is suitable for key exchange but is not protected against quantum attacks.
- Post-Quantum Encryption (PQC) prepares for quantum computers and combines classical and new methods for long-term security.
The combination of these standards provides comprehensive protection for sensitive customer data. Now is the right time to switch to quantum-safe methods.
1. TLS/SSL
TLS/SSL ensures secure data transmission in e-commerce by guaranteeing confidentiality (protection against unauthorized eavesdropping), integrity (prevention of manipulation), and authenticity (verification of website identity)[2]. You can recognize a secure connection by “https://” and the lock symbol in the address bar.
Security Strength
Since 2018, TLS 1.3 has been the current standard and offers significantly higher security compared to TLS 1.2 and outdated SSL versions[8]. By utilizing Perfect Forward Secrecy (PFS), past sessions remain protected even if the private key is later compromised[8]. Additionally, insecure algorithms such as MD5, SHA-1, RC4, and static RSA key exchanges have been completely removed. In 2022, the BSI also removed the hash function SHA-224 and the elliptic curve secp224r1 from its minimum standards[7].
Computational Effort
The TLS handshake is the most computationally intensive part, as it involves several steps. TLS 1.3 optimizes this process with only one Round-Trip Time (RTT) – compared to the two RTTs in TLS 1.2. In resumptions, a 0-RTT connection is even possible[8]. After the handshake, symmetric encryption works particularly efficiently. Session identifiers further improve performance by caching security parameters, making the complete handshake unnecessary for later connections[6].
Implementation Complexity
Setting up TLS requires managing the Certificate Chain. Your server transmits its certificate along with intermediate certificates to establish a trust path to a Root CA[6]. From April 2025, certificates will only be valid for 47 days, making automated management, for example via the ACME protocol, essential[8]. The BSI guidelines TR-02102-2 (Version 2025-1) provide clear recommendations on cryptographic mechanisms and key lengths[4][3]. These measures are crucial to ensure both the security of the connection and the trust in your platform.
Quantum Resistance
Another important aspect is the future threat posed by quantum computers. Current TLS 1.3 implementations rely on RSA and Elliptic Curve Diffie-Hellman (ECDHE), which are not resistant to attacks by quantum computers[8]. To remain protected in the future, e-commerce platforms must transition to Post-Quantum Encryption in the medium term.
At Gunfinder, we utilize the latest TLS/SSL standards to secure your transactions as best as possible.
2. RSA
RSA is an encryption method based on an asymmetric approach. It works with two keys: a public key for encryption and a private key for decryption. The security of RSA relies on the difficulty of factoring the product of two large prime numbers[11]. This principle makes RSA particularly suitable for applications where secure communication over insecure channels is required[13].
Security Strength
From January 1, 2026, the Federal Network Agency (BNetzA) and the Federal Office for Information Security (BSI) will require a minimum key length of 3,072 bits for companies and authorities[11]. However, many organizations are already using 4,096-bit keys to further enhance security[11]. Additionally, the use of Optimal Asymmetric Encryption Padding (OAEP) is recommended. This method formats messages before encryption to make mathematical attacks more difficult[10]. Despite these measures, RSA remains vulnerable to so-called side-channel attacks. In these attacks, adversaries analyze physical parameters such as power consumption or processing time to gain access to private keys[11].
Computational Effort
Compared to symmetric methods, RSA is significantly slower – about 1,000 times[9]. For this reason, RSA is usually only used in e-commerce for the secure exchange of keys. The actual data encryption is then performed with AES, which is better suited for bulk data[15]. However, during high data traffic, RSA handshakes can heavily burden server processors and lead to delays[15].
Implementation Complexity
Implementing RSA requires a robust PKI (Public Key Infrastructure) to manage certificates and secure digital signatures[5]. Another weakness lies in the potential threat from quantum computers. If they become powerful enough, they could bypass RSA-based protection by forging certificates. This would facilitate phishing and man-in-the-middle attacks[5].
Quantum Resistance
RSA offers no protection against quantum attacks. The Shor algorithm, when executed on a sufficiently powerful quantum computer, could solve the factoring problem in polynomial time. This would render RSA encryption insecure[11][12]. A concrete risk is the “Harvest Now, Decrypt Later” scenario. In this case, encrypted data intercepted today – such as customer data or contracts – could be decrypted in the future once quantum computers become available[16]. To prepare for this, e-commerce platforms should develop crypto-agile systems. These allow for a switch to quantum-safe algorithms without having to replace the entire infrastructure[16].
The next section will highlight the advantages and disadvantages of RSA compared to other standards.
3. AES-256
AES-256 is often referred to as the gold standard of data encryption and is used to secure highly sensitive information [14][17]. In e-commerce, it protects customer data and credit card information. With a key length of 256 bits, it offers a vast key space of 2^256 combinations – equivalent to about 78 digits. This enormous variety makes brute-force attacks practically impossible with today's computing power [13]. AES-256 combines high security standards with strong performance.
Security Strength
For e-commerce platforms, AES-256 is not only a security measure but also a regulatory requirement. The PCI-DSS standard mandates this encryption strength for the storage and transmission of payment card data [18]. Data breaches are an expensive problem in retail, and shockingly, 57% of data protection violations occur due to known but unaddressed security vulnerabilities [18]. AES-256 processes data in 128-bit blocks and goes through 14 encryption rounds – more than AES-128 (10 rounds) or AES-192 (12 rounds) [13]. These additional rounds further increase security.
Computational Effort
As a symmetric encryption method, AES-256 is significantly faster and more resource-efficient than asymmetric methods like RSA [15]. A study by Ryan Kovar from the Splunk SURGe team from March 2022 shows that AES-based encryption was able to process 100,000 files (53.93 GB) in just 42 minutes and 52 seconds [14]. This speed makes AES-256 ideal for e-commerce, where large amounts of data are processed without noticeably affecting system performance. Modern processors support AES-NI, further enhancing efficiency [14].
Implementation Complexity
The biggest challenge with AES-256 is key management. Since the same key is used for both encryption and decryption, it must be securely exchanged and stored between authorized parties [14][19]. Many e-commerce platforms therefore use a hybrid architecture: Asymmetric methods like RSA are used for the secure exchange of a session key, while the actual data transmission occurs with AES-256 [15][20]. Automated key rotation and secure storage in a vault system are essential, as the security of AES-256 entirely depends on the secrecy of the key [14][19]. Visible encryption like HTTPS is also business-critical, as over 51% of users abandon an online purchase if their browser displays a security warning [18].
Quantum Resistance
Compared to RSA, AES-256 offers better protection against quantum attacks. While asymmetric methods could be completely undermined by the Shor algorithm, the Grover algorithm only reduces the effective security of AES-256 to 128 bits. This level is still considered secure in the long term [16]. The Federal Office for Information Security (BSI) explicitly recommends the use of AES-256 in Technical Guideline TR-02102-1 (Version 2025-1) to protect digital information in the long term [1][3]. However, the overall security of a system also depends on key exchange. While AES-256 protects the data, Post-Quantum algorithms should be used for TLS handshakes to ensure complete quantum security [16].
sbb-itb-1cfd233
4. Post-Quantum Encryption
Post-Quantum Encryption (PQC) provides protection against quantum computers that can overcome classical encryption methods like RSA using the Shor algorithm [21]. The Federal Office for Information Security (BSI) puts it succinctly: It is no longer about “if” or “when” quantum computers will become a reality, but about addressing the transition to Post-Quantum Cryptography now [22]. Like TLS/SSL, RSA, or AES-256, PQC represents the next step in addressing future threats in digital commerce. The strength of PQC lies in mathematical problems that can withstand quantum attacks.
Quantum Resistance
PQC is based on mathematical challenges such as lattice problems, code-based or hash-based cryptography, which are difficult to solve for both classical and quantum computers [21]. In July 2022, the National Institute of Standards and Technology (NIST) standardized the first PQC algorithms. These include CRYSTALS-Kyber for key exchange and CRYSTALS-Dilithium, Falcon, and SPHINCS+ for signatures [21].
A benefit of PQC is that no special hardware is required – the algorithms can run on existing systems. The BSI recommends a hybrid approach: PQC methods should be used alongside classical methods to ensure long-term security even in the event of later discovered vulnerabilities [22].
Security Strength
A significant risk is that encrypted data intercepted today could be decrypted in the future by quantum computers. Attackers store such data with the intention of cracking it later [22]. For e-commerce platforms that need to protect customer data in the long term, this is particularly critical.
“The damage from data stolen today will only show in years – inaction is a catastrophic failure in risk management.” – Anand Oswal, Executive Vice President of Network Security at Palo Alto Networks [24]
While RSA is considered insecure against quantum attacks, AES-256 continues to be regarded as robust. Nevertheless, key exchange remains a vulnerability that must be made quantum-safe – this is where PQC comes in. In addition to increased security, efficient PQC algorithms allow for smooth integration into existing systems.
Computational Effort
Since PQC algorithms can be executed on classical hardware, they can be easily integrated into existing e-commerce infrastructures [21]. Particularly lattice-based methods like CRYSTALS-Kyber are considered efficient and are leading candidates for widespread use. However, the complexity of implementation varies: Hash-based signatures with state management, such as LMS and XMSS, require elaborate management and are therefore less suitable for applications where such control cannot be guaranteed [21].
To facilitate implementation, the BSI has integrated PQC methods into the open-source library “Botan”. This allows developers to test and apply these methods [21].
Implementation Complexity
The transition to PQC is a long-term project that affects thousands of devices, applications, and databases [24].
“The list is a necessary compliance step, but it's also an early market-shaping signal. The categories are broad, making it difficult for network engineers to identify what is actually required to provide PQC upgrades across networks, databases, and code repositories.” – Crick Waters, CEO of Patero [23]
Experts recommend two strategies: First, the development of crypto-agility, meaning the ability to swap algorithms without major changes. Second, the use of Cipher Translation to make older systems compatible. Companies should start with a comprehensive analysis of their cryptographic infrastructure, prioritizing key exchange [22][24]. With PQC, the security architecture is expanded to withstand future attacks.
Advantages and Disadvantages
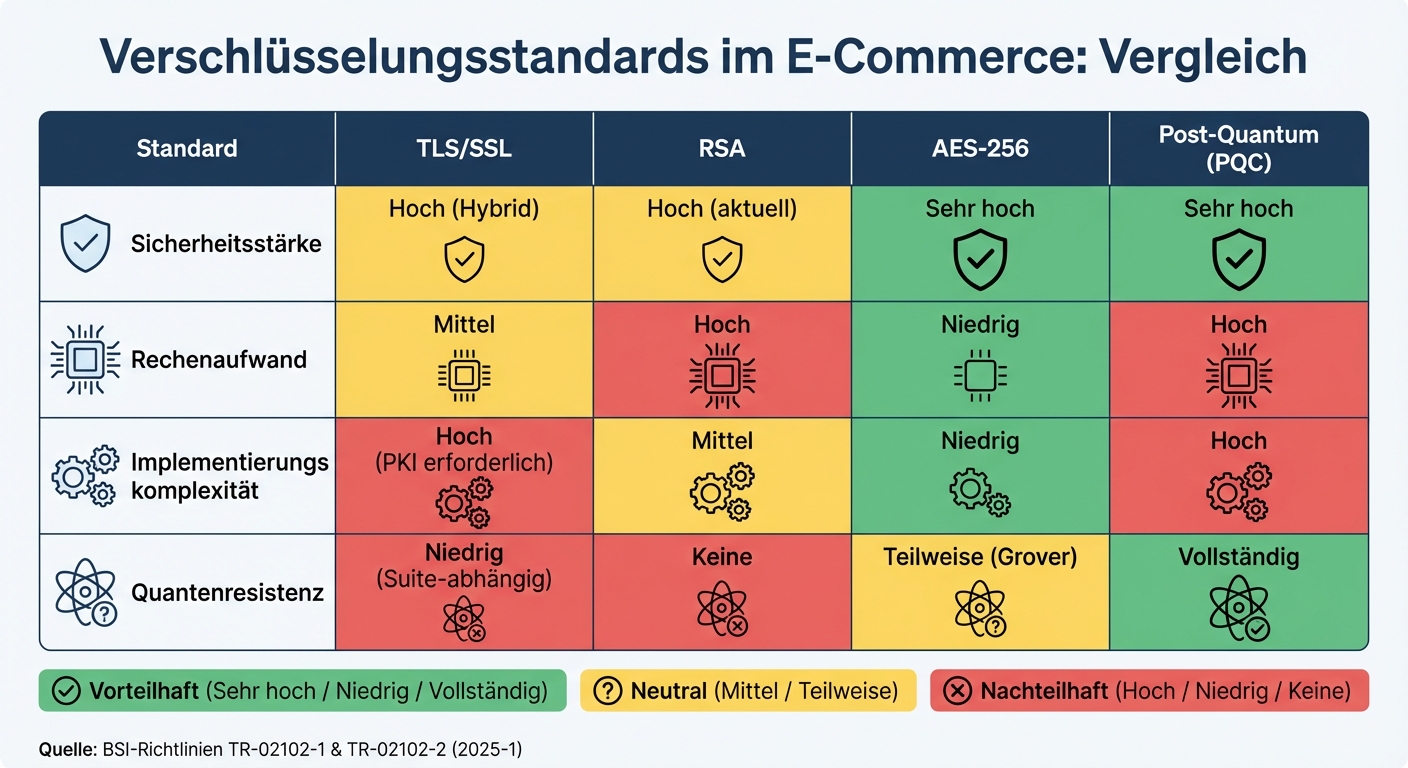
Comparison of E-Commerce Encryption Standards: TLS/SSL, RSA, AES-256, and Post-Quantum Encryption
Here is a brief summary of the strengths and weaknesses of the presented encryption standards to better understand their use cases.
TLS/SSL provides reliable protection for data during transmission and has established itself as the standard in e-commerce, especially for sensitive information such as credit card data and bank transactions [2]. However, the reliance on a Public Key Infrastructure (PKI) is a weakness: Invalid or untrusted certificates increase the risk of phishing and man-in-the-middle attacks [2][5].
RSA is based on public and private key pairs and enables secure digital signatures [5]. However, the high computational effort makes RSA less efficient than symmetric methods. Additionally, RSA is not protected against future attacks by quantum computers [25].
AES-256 impresses with its ability to encrypt large amounts of data quickly and efficiently. The secure key exchange is often supplemented by hybrid approaches [5]. However, AES-256 remains partially vulnerable to quantum computers, particularly due to Grover's algorithm.
Post-Quantum Encryption has been developed to withstand attacks from quantum computers [25]. However, the implementation of such algorithms is technically challenging and requires adjustments to existing protocols. Additionally, there is still uncertainty about which algorithms will represent the best choice in the long term [25].
The following table presents the key differences of the standards in a clear manner:
| Encryption Standard | Security Strength | Computational Effort | Implementation Complexity | Quantum Resistance |
|---|---|---|---|---|
| TLS/SSL | High (Hybrid) | Medium | High (PKI required) | Low (Suite-dependent) |
| RSA | High (current) | High | Medium | None |
| AES-256 | Very high | Low | Low | Partial (Grover) |
| Post-Quantum | Very high | High | High | Complete |
This comparison shows why hybrid approaches are indispensable in e-commerce. Platforms often combine RSA for secure key exchange with AES-256 for fast and efficient data transmission [5]. This way, the advantages of both methods are optimally utilized.
Recommendations
For secure transactions, you should use TLS 1.2/1.3 for data transmission and AES-256 for encryption. Sensitive transactions should only be protected by https://, and valid certificates from recognized certification authorities are essential [2]. Adhere to the requirements of the BSI guideline TR-02102-2 (Version 2025-1) [3]. These standards form the basis for the following recommendations.
Migration to Post-Quantum Encryption (PQC)
Start transitioning to Post-Quantum Encryption now before quantum computers become a reality. The CISA issued a directive in January 2026 requiring authorities to prioritize PQC-capable products in areas where they are already available [23]. Crick Waters, CEO of Patero, describes the significance of this list:
“The list is a necessary compliance step, but it's also an early market-shaping signal” [23]
Hybrid Approach for More Security
Combine quantum-resistant key exchange methods with classical algorithms to protect against both threat scenarios [22]. The BSI explicitly recommends:
“Post-quantum schemes should only be used in combination with classical schemes ('hybrid') if possible” [22]
Particularly important is the protection of key exchange, as this is where the risk of “store now, decrypt later” attacks is greatest [22].
Automated Tools and Modern Standards
Use automated tools to analyze your cryptographic infrastructure [23]. When purchasing new web servers or browsers, ensure that they already support NIST-standardized, lattice-based methods for key exchange. These are considered more technically mature than quantum-safe digital signatures [23]. Since January 2026, PQC-capable options for central web software have become widely available [23]. This not only strengthens your current infrastructure but also better prepares you for future challenges.
Long-term Suitable Methods and Key Lengths
Adhere to the BSI guidelines TR-02102-1, which define long-term suitable cryptographic methods and key lengths [3]. However, a joint market survey by the BSI and KPMG shows that the threat posed by quantum computers is often underestimated. Of over 150 questionnaires sent, only 28 responses were received [22]. Don’t wait any longer – start the migration today.
FAQs
How do you prepare your e-commerce platform for Post-Quantum Encryption?
To make your e-commerce platform fit for the era of quantum computers, you should closely examine the current recommendations from the Federal Office for Information Security (BSI). The BSI suggests using hybrid encryption solutions. These combine classical cryptography with post-quantum algorithms to create a secure transition phase. An important step is to adjust the key sizes according to the latest requirements and to use proven algorithms such as FrodoKEM or Classic McEliece.
Protocol Adjustments and Key Management
In addition to introducing new algorithms, you must also revise existing cryptographic protocols. This includes the use of hash-based signatures, which are considered particularly resistant to attacks by quantum computers. Equally important is optimizing the processes surrounding key management to further enhance the protection of your data.
A Strategy for the Transition
A clear and timely strategy is crucial to ensure a smooth transition. This way, you can ensure that your customers' data remains protected in the future – even when quantum computers eventually become commonplace. Those who act now will remain secure in the long term.
Why is AES-256 so important for protecting data in e-commerce?
AES-256 is one of the most secure encryption standards and is indispensable in e-commerce as it reliably protects sensitive data such as payment details and personal information. With a 256-bit key length, it offers an extremely high level of security that is practically impossible to overcome.
For platforms like Gunfinder, which work with confidential data, strong encryption is crucial. It not only helps to strengthen user trust but also meets data protection requirements. AES-256 ideally combines efficiency and security.
What difficulties can arise when implementing TLS 1.3?
The implementation of TLS 1.3 presents several challenges. One of them is adapting existing systems to the new security standards, which can often be time-consuming and technically demanding. Older applications or devices, in particular, may pose difficulties as they may not be fully compatible with TLS 1.3.
Another point is that implementation often requires an update of the entire infrastructure. This makes careful planning and extensive testing essential to ensure a smooth transition. Despite these hurdles, the effort is worthwhile: TLS 1.3 offers both improved security and noticeably better performance.